Trusted by Millions
Get easy-to-use, easy-to-install antivirus protection against advanced online threats. Plus online privacy and identity protection with select plans.
See offer details below.*
Compare plans
Automatically renews at
{ar}/year, unless the renewal is cancelled.
Price is subject to change.
Subscription details below.*
- 1 PC, Mac, tablet, or phone
- Antivirus, malware, ransomware, and hacking protection
- 100% Virus Protection Promise2
- 2GB Cloud Backup‡‡,4
- Password Manager
Automatically renews at
{ar}/year, unless the renewal is cancelled.
Price is subject to change.
Subscription details below.*
Automatically renews at
{ar}/year, unless the renewal is cancelled.
Price is subject to change.
Subscription details below.*
- 1 PC, Mac, tablet, or phone
- Antivirus, malware, ransomware, and hacking protection
- 100% Virus Protection Promise2
- 10GB Cloud Backup‡‡,4
- Password Manager
- VPN private internet connection
Automatically renews at
{ar}/year, unless the renewal is cancelled.
Price is subject to change.
Subscription details below.*
Automatically renews at
{ar}/year, unless the renewal is cancelled.
Price is subject to change.
Subscription details below.*
- 5 PCs, Macs, tablets, or phones
- Antivirus, malware, ransomware, and hacking protection
- 100% Virus Protection Promise2
- 50GB Cloud Backup‡‡,4
- Password Manager
- VPN private internet connection
- Parental Control‡
- Dark Web Monitoring§
Automatically renews at
{ar}/year, unless the renewal is cancelled.
Price is subject to change.
Subscription details below.*
Automatically renews at
{ar}/year, unless the renewal is cancelled.
Price is subject to change.
Subscription details below.*
- 10 PCs, Macs, tablets, or phones
- Antivirus, malware, ransomware, and hacking protection
- 100% Virus Protection Promise2
- 200GB Cloud Backup‡‡,4
- Password Manager
- VPN private internet connection
- Parental Control‡
- Dark Web Monitoring§
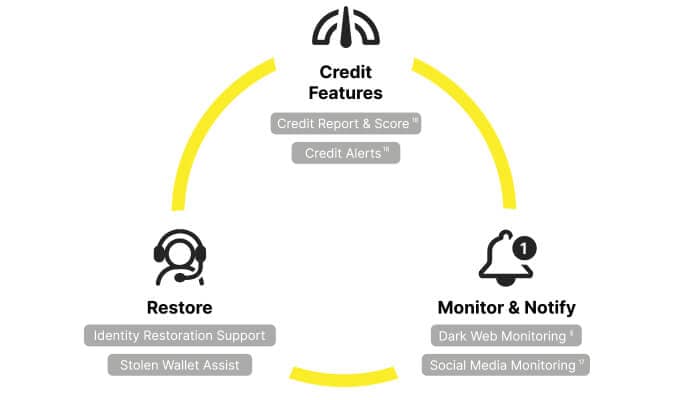
- Identity Restoration Support
- Credit Report and Score18
- Credit Alerts18
- Stolen Wallet Assist
- Social Media Monitoring17
- NEW! Financial Monitoring

Norton™ 360 Plans
Devices + online privacy protection
Device security helps block hackers and Norton Secure VPN helps you keep your online activity private.

Norton™ Secure VPN Plan
Online privacy protection
Norton Secure VPN helps block hackers from seeing what you do online, over public or even home Wi-Fi.
Norton™ Identity Advisor Plus
Help with identity theft starts here
Norton™ Identity Advisor Plus includes identity protection features to help you monitor and respond to identity threats and now with tools to keep tabs on your financial health!
Trusted by millions of customers.
Norton technology blocks thousands of threats every minute.
Count on decades of experience and a proven track record of keeping people safer every day.
Get the protection you and your family need in one place.
PC Mag:
A trademark of Ziff Davis, LLC. Used under license. Reprinted with permission. © 2024 Ziff Davis, LLC. All Rights Reserved.
AV-TEST
"Best Protection 2022 Award" for Norton 360
January - December 2022.
SE Labs
Best Home Anti-Malware 2023 for Norton 360
* Important Subscription, Pricing and Offer Details:
- Details: subscription contracts begin when the transaction is complete and are subject to our Terms of Sale and License & Services Agreement. For trials, a payment method is required at sign-up and will be charged at the end of the trial period, unless cancelled first.
- Renewal: subscriptions automatically renew unless the renewal is cancelled before billing. Renewal payments are billed annually (up to 35 days before renewal) or monthly depending on your billing cycle. Annual subscribers will receive an email with the renewal price beforehand. Renewal prices may be higher than the initial price and are subject to change. You can cancel the renewal as described here in your account or by contacting us here.
- Cancellation & Refund: you can cancel your contracts and get a full refund within 14 days of initial purchase for monthly subscriptions, and within 60 days of payments for annual subscriptions. For annual renewal payments (including post-trial payment), you can get a pro-rated refund of the remaining months left in your term. For details, visit our Cancellation & Refund Policy. To cancel your contract or request a refund, click here.
2 Virus Protection Promise: To be eligible, you must have a qualifying subscription with automatic renewal. If a Norton expert is unable to remove the virus from your device, then you may receive a refund based on the actual price paid for the current term of your qualifying subscription. If you have a bundle (a qualifying subscription from Norton purchased with either another offering from Norton, or a third party offering), your refund will be limited to the Manufacturer’s Suggested Retail Price of only your qualifying subscription for the current term, not to exceed the total bundled price paid. Any refund will be net of any discounts or refunds received and less any shipping, handling and applicable taxes, except in certain states and countries where shipping, handling and taxes are refundable. The refund does not apply to any damages incurred as a result of viruses. See Norton.com/guarantee for complete details.
4 Cloud Backup features are only available on Windows (excluding Windows in S mode, Windows running on ARM processor).
5 SafeCam features are only available on Windows (excluding Windows in S mode, Windows running on ARM processor).
8 Video Supervision requires a browser extension on Windows and the in-app Norton Browser on iOS and Android. It monitors videos viewed on YouTube.com (but not YouTube videos embedded in other websites or blogs) and on Hulu.com (but only on Windows). It does not work with the YouTube or Hulu apps.
16 To suppress most alerts for Windows, full-screen mode must be in use.
17 Social Media Monitoring is not available on all social media platforms and the features differ between platforms, for details go to: norton.com/smm. Does not include monitoring of chats or direct messages. May not identify all cyberbullying, explicit or illegal content or hate speech.
18 Norton Credit Portal features can be accessed following successful registration and verification. Available to those over 18, who are residents of UK, IOM & Channel Islands. Full Terms and conditions apply. Norton Credit Portal features are provided by TransUnion International UK Limited, which is registered in England and Wales with company number 3961870 and is authorised and regulated by the Financial Conduct Authority under registration number 737740. Financial Conduct Authority authorisation can be checked on the Financial Services Register at www.fca.org.uk.
γ Norton Safe Search does not provide a security rating for sponsored links nor does it filter out potentially unsafe sponsored links from the search results. Not available on all browsers.
‡ Norton Family/Parental Control can only be installed and used on a child’s Windows™ PC, iOS and Android™ device but not all features are available on all platforms. Parents can monitor and manage their child’s activities from any device – Windows PC (excluding Windows in S mode), Mac, iOS and Android – via our mobile apps, or by signing into their account at my.Norton.com and selecting Parental Control via any browser. Mobile app must be downloaded separately. The iOS app is available in all except these countries.
Popular browsers are supported, including Chrome, Edge, and FireFox. Parental Control portal access is not supported on Internet Explorer. On iOS and Android, the in-app Norton Browser must be used to get the full benefit of the features.
‡‡ Requires your device to have an Internet/data plan and be turned on.
§ Dark Web Monitoring is not available in all countries. Monitored information varies based on country of residence or choice of plan. It defaults to monitor your email address and begins immediately. Sign in to your account to enter more information for monitoring.
Δ 24/7 Support is available in English only. See https://www.norton.com/globalsupport. Identity Restoration Support is only available 9:00 - 18:00 GMT (Mon-Fri), as they are not available 24/7.
The Norton brand is part of Gen.
Copyright © 2024 Gen Digital Inc. All rights reserved. Gen trademarks or registered trademarks are property of Gen Digital Inc. or its affiliates. Firefox is a trademark of Mozilla Foundation. Android, Google Chrome, Google Play and the Google Play logo are trademarks of Google, LLC. Mac, iPhone, iPad, Apple and the Apple logo are trademarks of Apple Inc., registered in the U.S. and other countries. App Store is a service mark of Apple Inc. Alexa and all related logos are trademarks of Amazon.com, Inc. or its affiliates. Microsoft and the Window logo are trademarks of Microsoft Corporation in the U.S. and other countries. The Android robot is reproduced or modified from work created and shared by Google and used according to terms described in the Creative Commons 3.0 Attribution License. Other names may be trademarks of their respective owners.