What is phishing and how not to fall for it?
Billions of phishing links are shared each year—and when people engage with them, it can start a process that can end with malware infections, stolen funds, or even identity theft. Learn the meaning of phishing, how to identify an attack, and what to do if you click a suspicious link. Then, level up your online defences by using comprehensive cybersecurity.

Sometimes, you’ll receive legitimate links via text or email—maybe when your order is ready for pickup, a bill is due, or one of your co-workers wants to share an attachment. Unfortunately, legitimate links can be tough to distinguish from phishing links that are designed to scam, steal personal information or infect devices.
What is phishing?
The definition of phishing is a social engineering cyberthreat where scammers impersonate a trustworthy source and trick you into revealing sensitive data like passwords, credit card numbers, or personally identifiable information.
A phishing attack often starts with a scammer sending a malicious link or attachment via email, social media, or text, possibly triggering a malware download. Scammers will often pose as well-known names to lure you into their trap — sometimes even impersonating trustworthy brands like Norton to try to scam you.
Alternatively, you may receive a phishing call that comes from a phisher pretending to offer customer service or tech support.


How does phishing work
While phishing can vary based on the specific type of scam the scammer is carrying out, a phishing attack often follows these steps:
- The phisher selects a target (this can be an organisation, group, or individual) and comes up with a ruse.
- Next, the phisher chooses a communication method and makes contact.
- If effective, the target will engage by replying, opening the phishing link, or downloading a malicious attachment.
- Finally, phishers will collect data and use it to make illegal purchases or commit fraudulent acts such as identity theft.
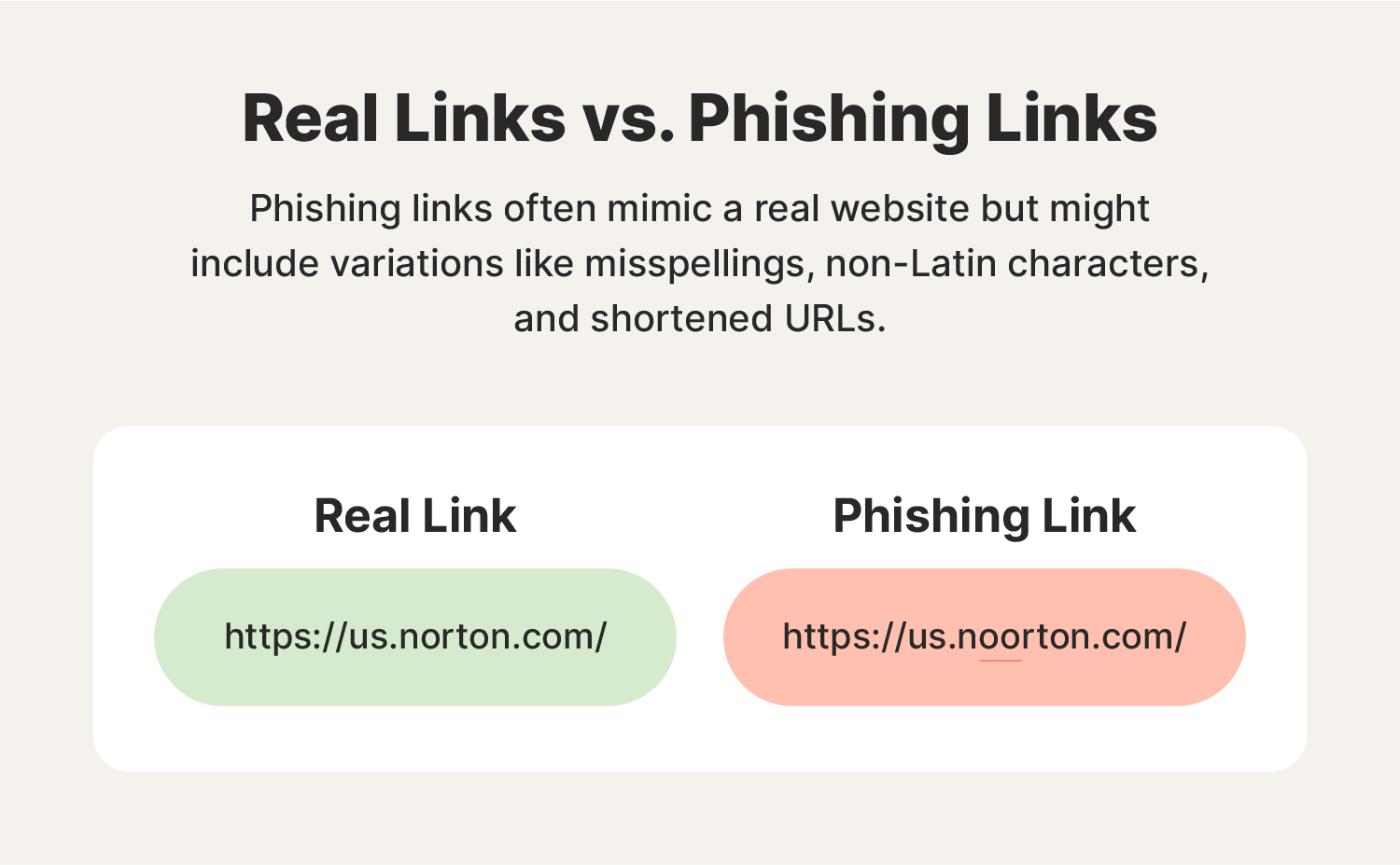
What is a phishing link?
A phishing link is, by definition, a fake link used by cybercriminals to trick you into compromising your own privacy and security. Clicking a phishing link may install malware on your device, or guide you to a spoofed website where you’re prompted to enter sensitive information.

What is a phishing attack?
Phishing scams can take many forms—the type of individual attack ultimately depends on the phisher, who they target, the communication platform they use, and their end goal.
Here’s a rundown of a few predominantly link-based phishing attacks.
Email phishing
The basic phishing email is sent by fraudsters impersonating legitimate companies, often banks or credit card issuers. These email phishing examples trick you into providing sensitive information by getting you to download malware unknowingly or by directing you to an unsafe website where you’re asked to voluntarily enter private information.
Spear phishing
Spear phishing emails target a specific individual, business, or organisation rather than just casting a wide net. Typically, spear phishers invest a lot of time and effort into researching their targets and building a credible persona. For example, the attacker may assume the identity of your boss and trick you into revealing proprietary information in what you believe to be an internal conversation.
Clone phishing
In clone phishing attacks, scammers create a nearly identical version of an email that victims have already received. The cloned email is sent from an address that is nearly, but not quite, the same as the email address used by the message’s original sender. The body of the email looks the same, too.
What’s different about a clone phishing attack is that the attachment or link in the message has been changed. If victims click those links now, it will take them to a malicious website or open an infected attachment.
Whaling
Whaling attacks target chief executive officers, chief operating officers, or other high-ranking executives. The goal of a whaling attack is to trick powerful people into giving up sensitive corporate data. By definition, these phishing attacks are more sophisticated than general phishing attacks and require plenty of research from scammers. They usually rely on fraudulent emails that appear to be from trusted sources within the company or from legitimate outside agencies.
Pop-up phishing
Pop-up ad phishing scams trick people into installing various types of malware on their devices by leveraging scare tactics. A common pop-up phishing example is when a fake virus alert pops up on a user’s screen warning the user that their computer has been infected and the only way to remove the virus is by installing a particular type of antivirus software. Once the user installs this fake software, it either doesn’t work or, worse, actually does infect the computer with malware.
What techniques do phishers use to manipulate their targets?
To help increase their chances of getting the information they want, scammers may employ a combination of different phishing techniques, including:
- Social engineering: This is the act of tricking someone into divulging sensitive information using manipulative persuasion tactics. For example, a scammer may pretend to be a family member in a dangerous situation to try to get you to quickly send them money.
- Hyperlink manipulation: Phishers may use the text of a legitimate URL to disguise a link to a phishing website. For example, you may think you’re navigating to your bank’s official support page, but after hovering over the link, you discover it is actually going somewhere else.
- Graphical rendering: This happens when a phisher uploads their email as an image rather than text to prevent certain text from being scanned by phishing filters.
- Site redirects: Phishers may also use a malicious webpage as a middle ground between their phishing email and a legitimate site. For example, following their instructions may take you to a webpage created by a phisher to collect your personal information before redirecting you to a legitimate website to minimise your suspicion of a phishing attack.
- Link shortening: Another popular phishing tactic is using link shortening tools to disguise links to dangerous websites.
- Typosquatting: By using typosquatting, a phisher registers domains that are very close to a legitimate domain, hoping their targets won’t notice. For example, a phisher pretending to be an Amazon support representative might create a phishing site under the URL “Amazpn.com.”
- AI voice generators: Phishers may use AI voice generators to impersonate public figures or acquaintances of yours to get you to divulge sensitive information.
- Chatbots: Scammers may also use AI-enabled chatbots to create highly personalised phishing messages free of the kind of spelling and grammatical errors often associated with phishing attacks.
Now that you better understand the techniques used by phishers, it’s time to learn the common warning signs of a phishing attack.
What to do if you clicked on a phishing link
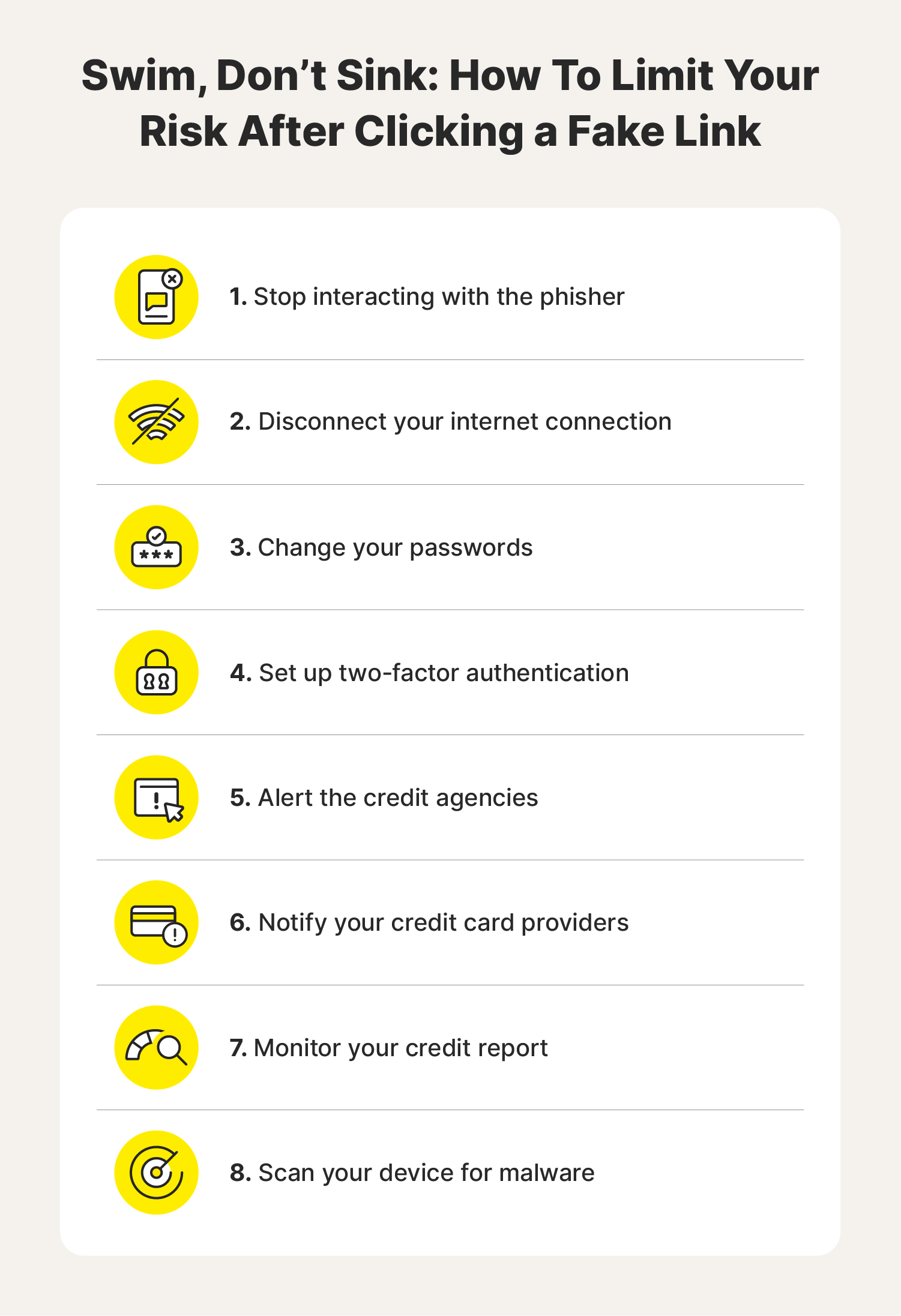
If a phishing scam lures you into clicking a malicious link, it’s important to act quickly to minimise the fallout. First, cease all interactions—stop communicating with the attacker, end any active downloads, and close out of the spoofed website if the URL took you to one. Then, secure your device and begin the process of monitoring your credit and other accounts for signs of fraud.

Stop interacting
If you realise you fell into a phishing trap, immediately stop what you’re doing. Depending on the situation, this could mean closing the spoofed website window or halting an in-progress download. Ending the interaction after clicking a phishing link can help protect your data by preventing sensitive information from being transmitted to the attacker.
Disconnect your internet
Disconnecting your internet connection after clicking a phishing link is another way to stop ongoing data transfers. This is a good option for stopping background processes and preventing malware from spreading to other devices on your network.
Change your passwords
Prevent ongoing unauthorised access to your accounts by changing any account login credentials that may have been compromised when you clicked a phishing link. To help block hackers, craft long and unique passwords, mixing uppercase and lowercase letters, numbers, and symbols for maximum security.
Enable two-factor authentication (2FA)
If you recently clicked a phishing link, consider adding a further layer of protection to your accounts with two-factor authentication. This helps keep your accounts safer even if a hacker gets their hands on your password, because 2FA requires users to enter a secondary verification code sent directly to an alternative device.
Alert the credit agencies
Visit the home pages of the three national credit agencies—Experian®, Equifax®, and TransUnion®—to alert them of the phishing attack and freeze your credit. Freezing your credit helps ensure criminals can't open new credit accounts or take out new loans in your name.
Contact your credit card issuers and review your statements
If you shared your credit card information with a phisher, contact your credit card issuer. They can help you freeze your credit card to stop unauthorised purchases and help you comb through your statements to identify fraudulent transactions. They may even be able to reimburse you for purchases the phisher made using your card.
Check your credit report
Check your credit report regularly for signs of identity theft and financial fraud in the months after clicking a phishing link. This is where you’ll see if someone applies for loans or takes out lines of credit in your name.
Report the phishing attack
Mark as spam or junk any phishing messages or calls you see. Then, report the phishing attempt to help counter-cybercrime groups track threats and limit future phishing attacks.
Here’s how to report phishing messages:
- Report phishing text messages by forwarding them to SPAM (7726).
- Report phishing emails to the National Cyber Security Centre (NCSC) by by forwarding the phishing email to report@phishing.gov.uk.
Scan your device for malware
Use antivirus software like Norton 360 Deluxe to help identify and block online attacks and help prevent phishers from continuing to spy on you or stealing your personal information.
How can I spot a phishing attack before clicking a link?
These days, phishers are much more adept at baiting their targets and luring them in. Still, there are several ways you can spot a phishing attack before it becomes a problem, including:
- Unbelievable deals: Be wary of emails offering wildly cheap products or services. If it seems too good to be true, it probably is.
- Requests for personal information: Legitimate institutions like banks will never ask for account details via email—never share such information this way.
- Spelling and grammatical mistakes: Emails littered with typos and awkward phrasing are common in phishing emails and text messages.
- Generic greetings: Many times, phishers don’t bother to personalise emails because they just want to cast a wide net and catch as many people as they can. So you might receive an email with a generic greeting like, “Hello, Sir” or “Dear Account Holder.”
- Urgent language: Phishers create urgency to rush you into clicking links. Don't be pressured; take your time when reading and responding to emails.
- Unfamiliar senders: Delete emails from unknown senders without clicking anything. This is especially important if you can’t verify their identity.
- Familiar senders: Even seemingly familiar email addresses can be fake. If the tone, communication channel, or content feels off, try to reach out to the person using another form of communication to confirm their identity.
- Suspicious links and attachments: Before clicking a link or downloading an attachment, hover over the link and inspect the URL for inconsistencies.
- Use a scam detection tool to analyse messages: If a message looks suspicious, use an anti-scam tool like Norton Genie to help determine if the message is legitimate.
How do I know if I clicked a phishing link?
You may not immediately realise that you clicked a phishing link because it can take some time for red flags to appear.
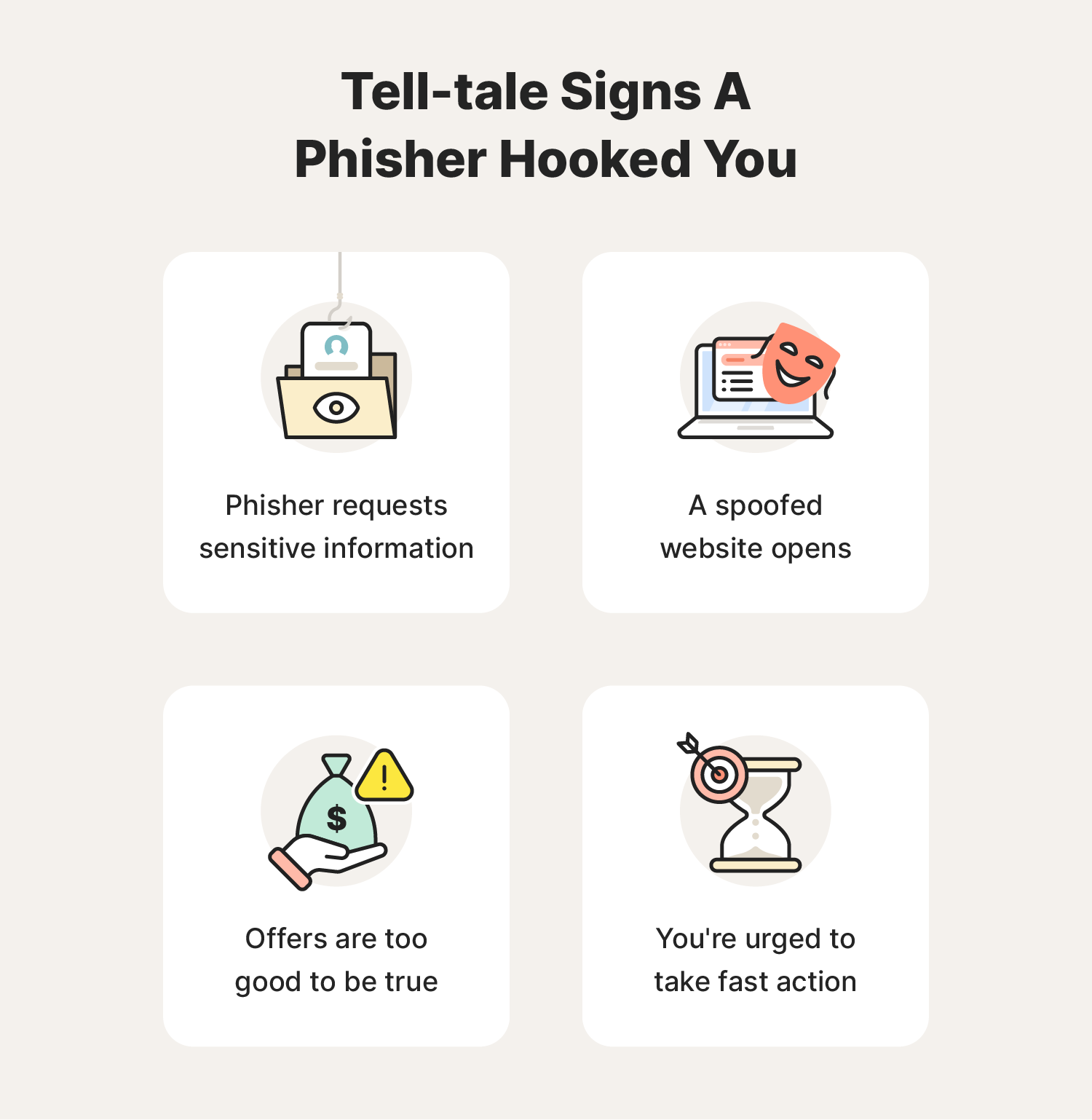

You’ll know you’ve likely been phished if you start noticing warning signs like:
- Suspicious redirects that take you to crudely made websites with misspellings and odd characters in the URL.
- Invasive personal information requests like a form prompting you to enter sensitive details like your National Insurance Number or account information.
- Too-good-to-be-true messages and offers like free holidays or job offers with sky-high salaries to try to entice you to engage with the phisher.
- High-pressure language in messages or website copy that creates a sense of urgency to encourage you to click a link without thinking.
Defend against online attacks with Norton
As cybercriminals continue to evolve their phishing attacks and other scams, you need advanced security software to help bolster your defences.
Norton 360 Deluxe helps you use your devices more safely, with powerful malware and virus protection, advanced anti-hacking features, and even a fake website blocker to help thwart attempts to steal your data.
FAQs about phishing
If your questions don’t just stop at “What is the meaning of phishing?” we’ve got you covered. Read through this FAQ section to learn more about phishing scams.
Who are the targets of phishing attacks?
Anyone can be targeted in a phishing attack. To increase their chance of success, phishers will often target as many email addresses or phone numbers as possible.
Can AI be used for phishing attacks?
Yes, scammers can use AI to make their communications sound more believable. For example, phishers may use it to generate realistic conversations free of spelling and grammatical errors so their phishing messages seem more legitimate.
Can you get scammed by opening a text message?
No, opening a scam text message itself isn't risky. However, clicking links within those text messages or replying can expose you to malware or trick you into revealing personal information.
What do you do when you click a suspicious link on your phone?
If you tap a suspicious link on your mobile, close the website, stop any active downloads, and disconnect your internet connection. Then, use security software to scan your phone for malware. Finally, change the passwords for any accounts that may have been impacted.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.
- What is phishing?
- What is a phishing attack?
- What techniques do phishers use to manipulate their targets?
- What to do if you clicked on a phishing link
- How can I spot a phishing attack before clicking a link?
- How do I know if I clicked a phishing link?
- Defend against online attacks with Norton
- FAQs about phishing









Want more?
Follow us for all the latest news, tips, and updates.